GDPR stands for General Data Protection Regulations and is the policies or rules or law for the protection of data from the European Union countries for uploading the privacy of the citizens in EU.
The regulation specifies private and governmental organizations to protect the privacy and personal data of EU citizens while processing and transfer of information contained by the EU and to the external side of the EU. It considers that the organizations protect privacy and personal data of EU citizens with a reasonable and appropriate level of controls.
Personal data includes data which identifies a person with a name, sex, Date of Birth, phone number and address, social security number, etc.
We've been a premier partner with Canva, using the free graphic design tool since it first launched. Canva is a free design tool that let's you design anything, for free.
GDPR applies to all the organizations that access, store, transmit and process the EU data inside and outside of EU.
GDPR will come into effect from 18th of May 2018.
Why Should You Use Data Mapping In Your GDPR Project?
The organization must record and keep the data flow and where, how and intent the data is accessed, stored, transmitted and processed. That information maintained must contain the following:
- a) The information including the address and name of the controller, joint controller and their representatives and Data Protection Officer;
- b) Data processing activity’s intent;
- c) A narrative of the classes of personal data and data subjects;
- d) The information on the disclosure of personal data of the EU subjects within EU and outside of the EU to any country or Organizations;
- e) The transfer of data within EU and outside the EU to any country or organizations where applicable,
- f) Management of data after the necessary work whether it has to be stored or retained or erased as per the agreement
- g) Technical information and other organizations control to govern the data where possible;
Essential Details of GDPR Data Mapping
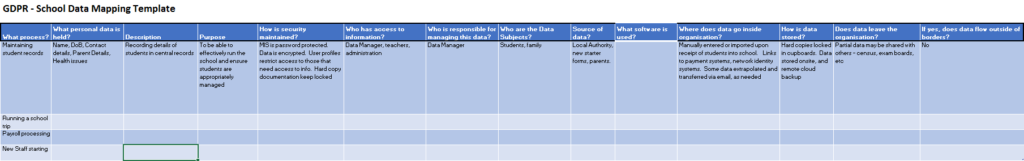
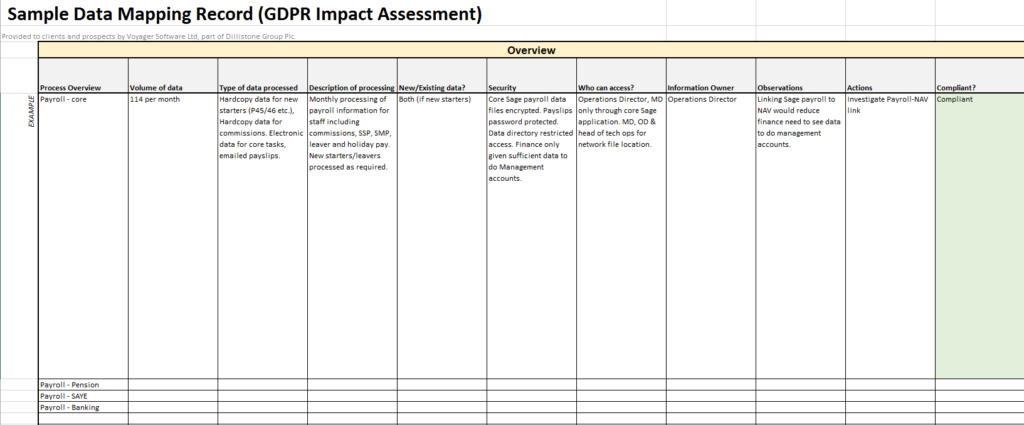
Data mapping identifies the data flow on from where the data flows to where and how the information is disclosed and to whom and how the information is accessed, how the information is stored and transmitted and processed. This is to identify any misuse of data and to safeguard the data. Data flow includes the controller, the processor and sub-processor and to customers.
A data map must abide by the below mentioned essential elements:
- The data( g., personal data such as name, address, phone number and social security number)
- The processor and the controller( from which organization the data originates and who process it)
- Formats of data (Data Base, Hardcopy, )
- Data transfer technique(g., airmail, emails, websites)
- Venue( g., Data Center, office, cloud or sub-processor)
The data flow map must outline all the necessary life cycle of the data, and the person holds the accountability for the data at any given point in time.
How To Data Map
Know the fundamental questions that need to be addressed by the organization?
- Nature of private data that gets collected? Does it contain sensitive private details?
- Which organization is collecting and using the data? Is the data sent to processor and sub-processor?
- If the transfer of data to a subprocessor or processor where are the subprocessor and processor located? Whether the data gets hosted in the processor’s or sub processor’s country outside of EU?
- How long the data is retained and how and when is the data collected?
- What is the purpose for which the data is collected and how it is used?
Data mapping and its advantages
Data mapping helps not only for the organization but also for the regulatory body and is significant during the breach. The advantages of the data mapping are listed as follows:
GDPR: The data mapping supports in compliance and adherence to some critical GDPR factors such as:
- Maintenance of the data lifecycle
- The records are kept in adherence to the rules of GDPR to submit to the regulatory and supervising authorities.
- Maintaining Accountabilities of the data for the full data lifecycle.
- Evidence for the organization and tells that the data is protected in its full cycle.
Other advantages:
- Shows improvement in various areas of the IT systems and business processes by regulating data flows in its life cycle.
- It mitigates the event of a data breach by data protection.
- Keeping records helps the organization to track the compliance and breach event discoveries with minimized costs.
- Helps in data lifecycle management and maintenance of procedures and policies or rules for GDPR.
Data mapping is essential to the organization for its compliance with the GDPR and streamlining the data flows and in general maintenance of data lifecycle management and also simplifying the business and IT systems. This is also helpful for the regulatory body or the supervisory authority and to mitigate the event and impact of the breach.
GDPR Data Mapping Requirement
Data mapping is an activity which requires help from various functions of the organization. Few dedicated staffs are needed for streamlining and maintenance of data flow and maintaining compliance with the requirement. This is an important workout, and the essentials of what we are achieving in the process are as follows:
- The importance of the PII being managed by the organization for the entire lifecycle of the information or data.
- Where is the data stored such as Tapes, Server, Desktops, Share points or Databases, ?
- Who are all responsible for the data in various time and life cycle of data?
- Who has the privilege to access information or data?
- Don’t forget to consider the data touch points and the systems interfaces along with the processor and sub-processors.
The best way to initiate is to talk to every person holding data and function or division head who is accountable for the data. For example, the HR may have data of on candidates and staff of the organization and most likely contain the PII information. This information needs to be secured. CRM may provide data on the key customers and may provide PII information. Functions may include data on social security number, Credit card number, and other sensitive PII information. All these data may be accessed, stored, transmitted and processed in one way or the other. There will be a lot of data touch point in the IT systems. Look for the weak controls and loophole in the policies and who owns the data and how can we mitigate the breach or such an event. One by one writes down on how the data lifecycle is and who is accountable for which sensitive data.
After the data mapping works out gets over, you will find much information on the data flow, who owns what and if there are any vulnerabilities. For example, HR systems may be accessed by IT professional and may have access to sensitive HR data. Whether the IT teams have the necessary privileges to access the HR data and whether HR team knows it? Also, do we have consent from the staff of the organizations to process the data or transmit the data to the partner organization? Similarly, the CRM and Operations data may be accessed by the sales team to selling the products or services. And whether the CRM and operations team know that another group such as sales team is accessing their data? These are some of the things which we need to work on.
Now, you will have complete information on the data flow on what are the data touch points such as the It systems and who owns or accountable for the sensitive data. Also after this exercise, you have required an amount of information, and you can start planning and putting controls where ever needed for the organization.
GDPR Risk Assessment Template
The risk assessment is a mandatory portion of every GDPR process. However, it is not defined on what constitutes risk assessment and what is the definition of risk?
This is because the GDPR applies to a wide variety of the organizations which has data and may be big or small. That is why there is a vague description of risk assessment and is called Data protection Impact assessment or risk assessment in general.
We need to adopt an approach considering the risk to align ourselves with GDPR requirements. Any risk identified by risk assessment or audit or Vulnerability Assessment or various other incidents must be defined, mitigated and reviewed periodically.
You can maintain a record such as a risk profile or risk register and Risk Assessment report which is done on a regular basis.
As per the GDPR we need to maintain all the risks that are assessed by the organization on the data flow and IT systems. Risk assessment is nothing but the risk-based approach to identify risk, mitigate risk by putting necessary control and then review the risks on a periodic basis.
There are various Risk Assessment frameworks such as ISO 31000, ISO 27005, etc. GDPR does not specify how to adopt the risk framework and which structure to choose. It is the independent decision of the organization to assume the risk assessment framework and methods.
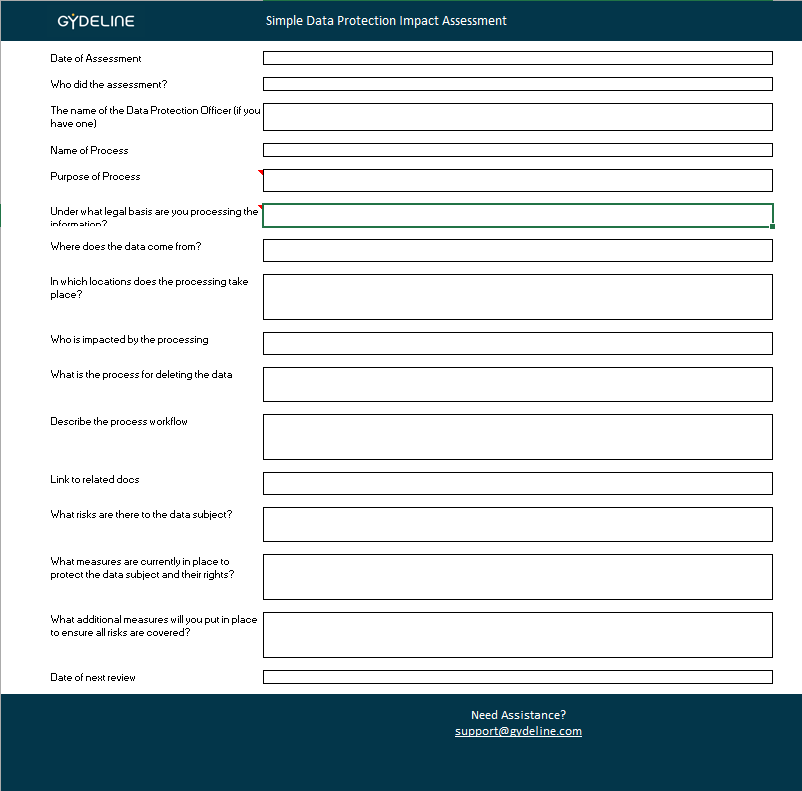
The risk assessment methodology consists of either a qualitative risk assessment or quantitative risk assessment. Please refer the risk assessment template to know more about this.
At the time of performing risk assessment, the organization needs to understand the complete data lifecycle and the person in charge of which data and when?
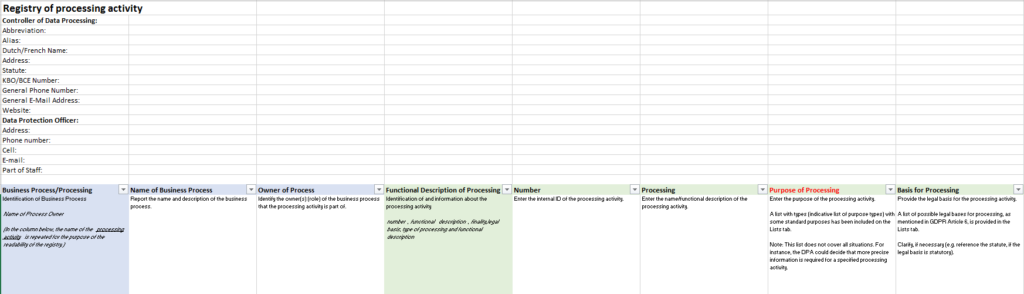
GDPR Article 30 Data Inventory
Article 30 has the following details documented
- The name and address of the stakeholders namely the data protection officer, joint controller, controller and their representatives;
- The intent of the data processing activity;
- A narrative of the classes of private data and persons concerned;
- Information on the transfer of personal data of individuals from the EU too and from the EU to a country or organization;
- Data transmission within and outside the EU to a country or organization, where appropriate;
- Data management after the necessary work, whether stored or deleted by the agreement
- Information on technical controls and those of other organizations to regulate data whenever possible;
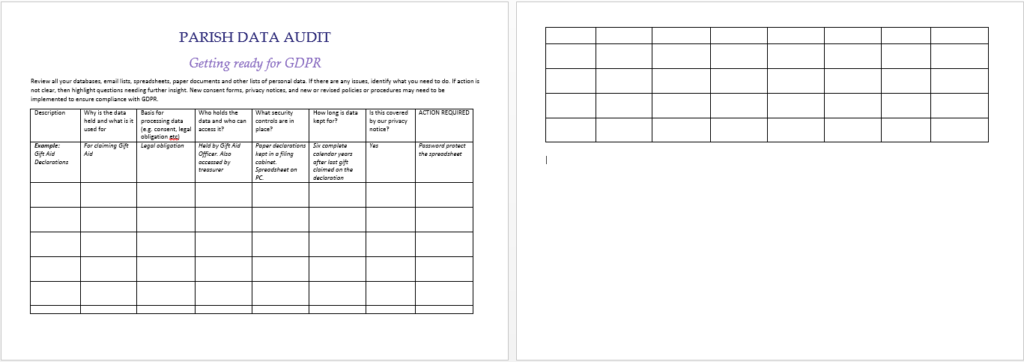
Information Audit GDPR
Information Audit is the review of the data flow and IT systems conducted to know the IT systems used incomplete data lifecycle management. Also, to understand from where the data originates, who access it, who process it how it is disclosed, how the data is transmitted, where it resides or stored and how it is handled and who is accountable for which information and when during the data lifecycle management.
We have created an audit template for use by all the customers. While conducting the audit, the following questions can be addressed
- What type of sensitive PII data exists?
- What is the format the data exists?
- Where does the data originate?
- Who has access to data?
- What is the timeframe for accessing the data?
- What is the rank of access to the PII data?
- Whether consent was obtained to store, transmit access, disclose and process the data?
- Where is the data transmitted?
- What are the controls, policies, and procedures to keep the data secured?
- Where is the data hosted?
- Where and how is the data processed?
- How is the data disclosed?
- What are the IT systems for data touch points?
- Who else may have access to the same data?
- Who is accountable for what data?
- What is the data retention timeline?
- How is the data destroyed or given back if not needed?
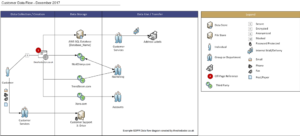
Data Mapping Process Flow
The data mapping process flow is explained in 5 steps as follows:
Determine the data lifecycle and scope of all the PII data that exist in the organization.
In detail determine the all the processes of the organization explicitly detailing who is accountable for which step and also what are the asset used in each process.
After the processes are mapped determine what is the Personally Identifiable Information (PII) that exists for the each of the operations.
Then add the assets used for processing the PII data in a particular process for the given scope. Enlist the functions, applications and devices and other assets used for treating the PII data.
Now determine how the PII data flows across the IT systems or assets. How it is transmitted and the ways employed to transfer the data.
Finally, evaluate the process and show it to the relevant stakeholders. Then visit these five steps again and again either periodically whenever there are changes in the process, assets or data.
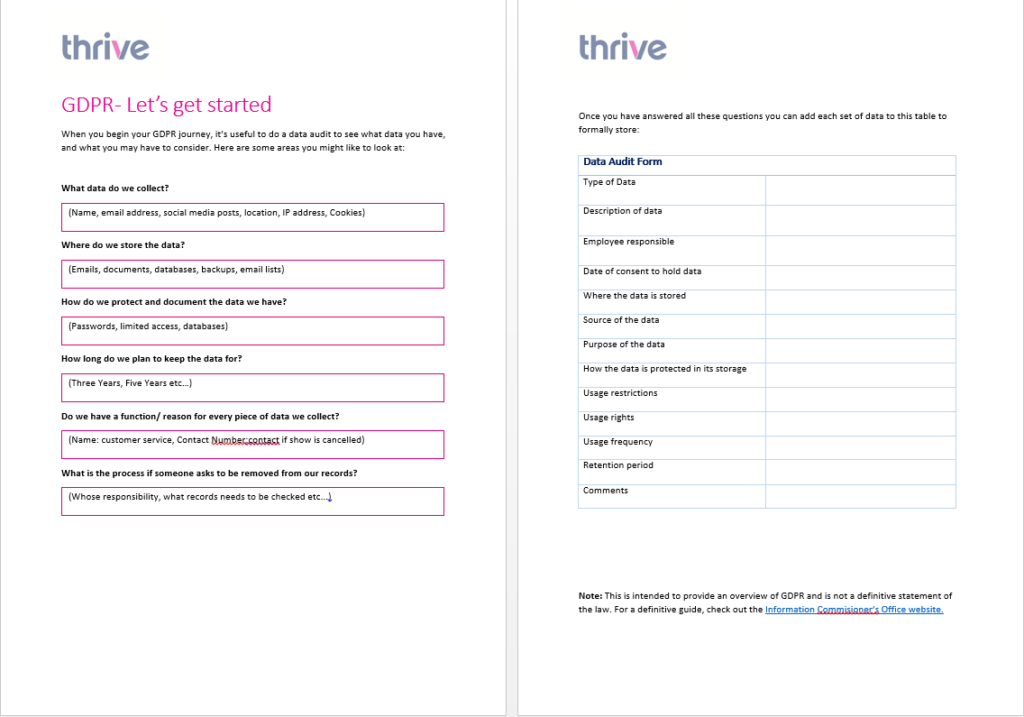
Data Audit Template
The data audit template is attached along with this document. Please refer the audit template and the questions asked for the audits in the section above.
In the audit, you may come up with the noncompliance to specific areas of GDPR regulations, document it and then put appropriate and reasonable controls to safeguard the data as per the GDPR regulations. You may also find that specific process has become obsolete in that case document and then remove the process. You also need to see the Data Privacy policy for securing the data in your organization. It is mandatory for the controller to appoint a Data Protection Officer responsible for GDPR adherence and compliance.
GDPR Data Mapping Summary
Data mapping summary give a lot of information about the PII data in the organization. Also provides information on what and which records to keep for the easy compliance and discoveries of the data flow. It also provides the complete picture of what PII data is accessed, owner and data lifecycle.
Summary of Data mapping is given in 5 steps as follows:
- Talk to the relevant stakeholders in your Organization for discussion on the sensitive PII data.
- Record the data flow about the sensitive PII data, its owner, and complete data lifecycle.
- Determine the vulnerabilities and system weaknesses around the access control. Transfer to unauthorized and unsecured systems, and to processor and sub-processor.
- Record the flow of data into and out of the organization.
- Take necessary sign-off from the accountable and owner of the data. Data protection is the collective responsibility all people working in the organization and just not few.